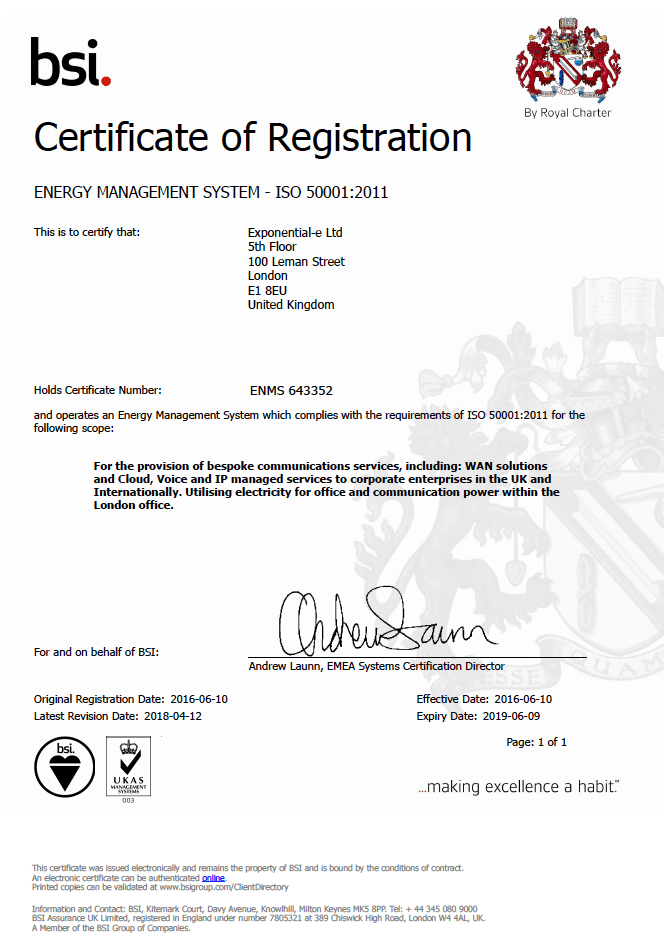
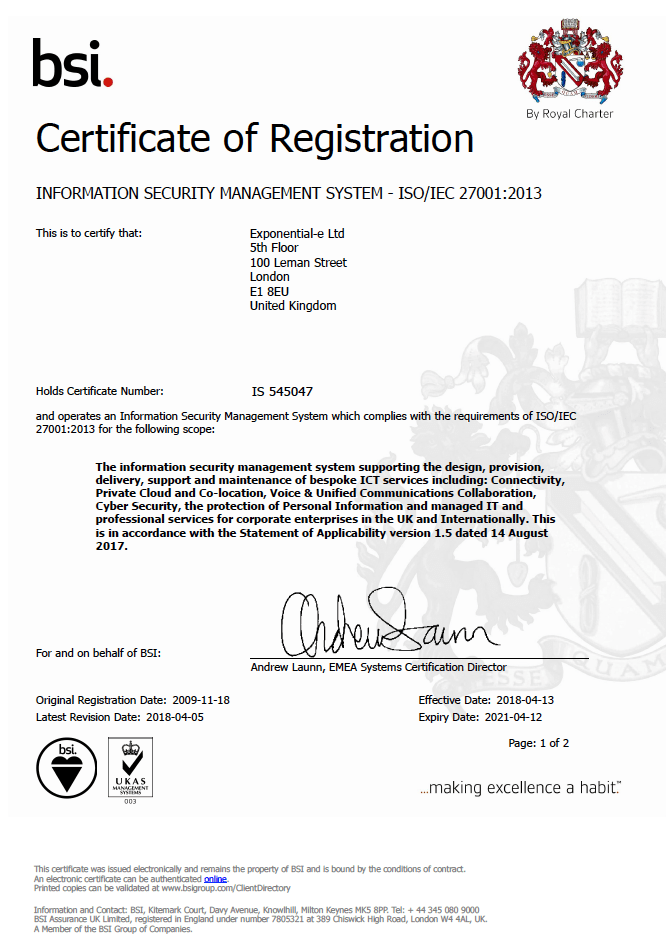
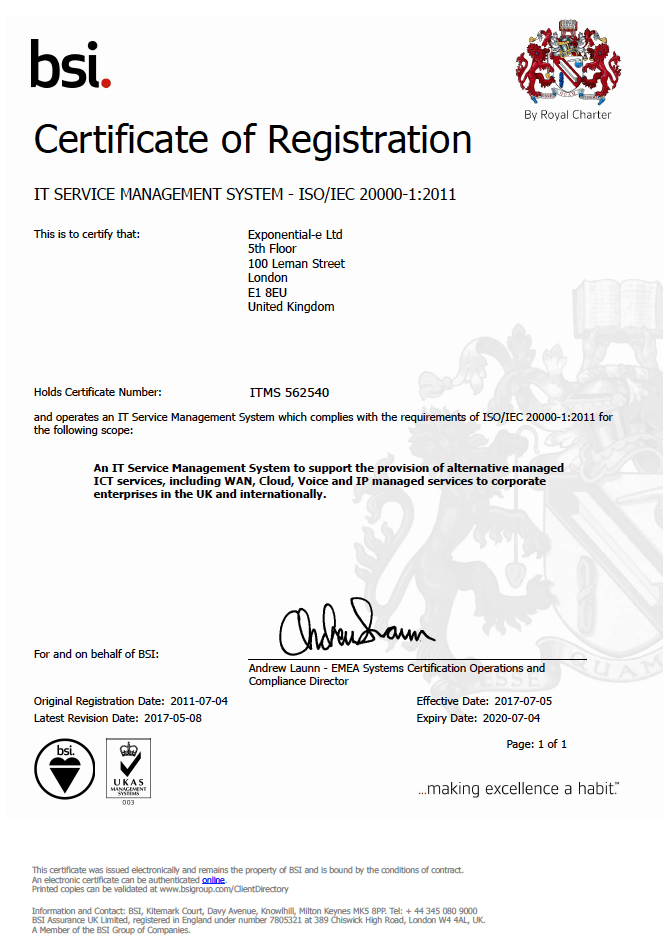
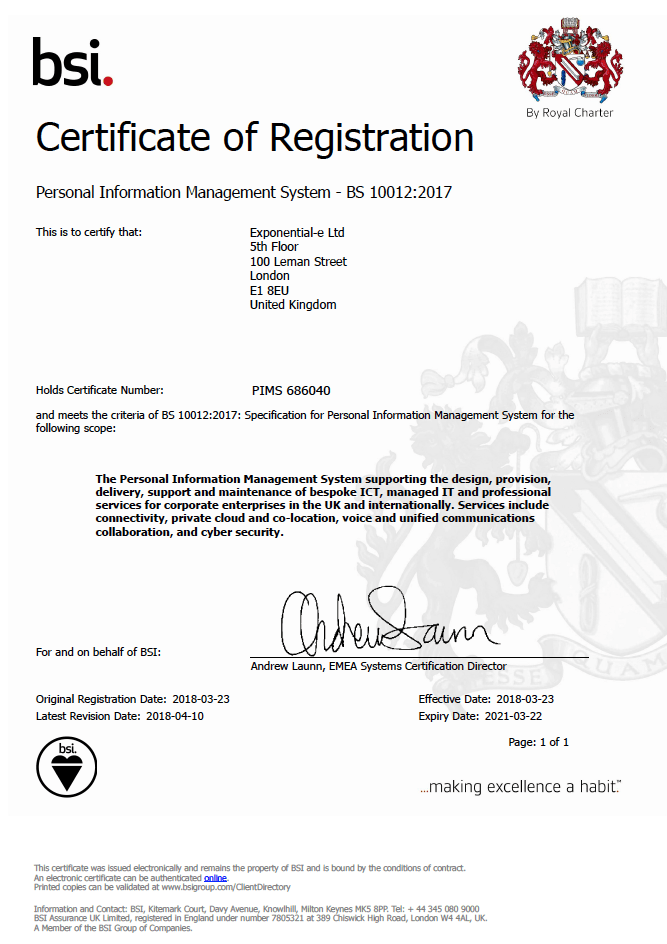
Securing Peace of Mind for Pension Schemes Trustees with Exponential-e.
Is your scheme ready for the TPR’s new regulation on cyber security?
Protect from cyber threats
Trustees’ duties and obligations
in a new digital world
The obligations and fiduciary duties trustees have to beneficiaries have materially changed with the rise of increasingly interconnected technologies and the proliferation of personal data transfers. This is the new world we work in, and the way we secure critical data must evolve accordingly.
The Pension Regulator’s General Code Of Practice is the foundation to predicate your scheme's strategy upon. An initial internal and external risk GAP analysis and readiness assessment for Cyber Essentials is a natural place to start working towards an accessible, low-cost accreditation for basic IT security. We can help your scheme achieve compliance for sections pertaining to cyber security and IT maintenance within the new General Code of Practice from the Pensions Regulator, working with you and your service providers to deliver a roadmap that protects the IT integrity of your scheme and the individual trustees who run it.
Exponential-e offers support in many other ways - but it must fit your scheme’s specific needs and strategy. We are non-prescriptive in our services and only advocate what is best for your scheme. Having a bespoke blend of appropriate and proportionate IT services, training and risk assessment will help your scheme defend, respond and operate effectively in the new digital world. We can work together, step by step, to mitigate your liability and guard the assets you dutifully protect.
When you are fighting against unknown unknowns and bad actors, it helps to have an experienced eye watching out for you and your beneficiaries.
And we will do just that.
Tools to Secure Your Scheme’s Future
How can you effectively protect yourself in a constantly evolving cyber threat landscape, mitigating liability and the risk of attack? We recommend utilising these five foundational solutions as the basis of your evolving cyber security ecosystem:




Cyber Security Consultancy (Maintenance of IT systems & Cyber Controls)
You should ensure sufficient understanding of your cyber risk._The Pensions Regulator
As prescribed by the Pensions Regulator, an initial gap analysis conducted by Exponential-e will help you build a mature risk assessment policy. This will help achieve best practice and deep industry experience around IT risk within your scheme’s internal and external operations and processes. We advocate performing a review to establish where you are today vs. where you need to be, in order to maintain compliance.
For internal aspects, Cyber Essentials is the industry-leading standard for basic cyber security, provided by the NCSC (National Cyber Security Centre). Exponential-e provides a comprehensive readiness assessment, conducted by an IT security expert, ensuring that your scheme will be 100% prepared to pass the Cyber Essentials self-assessment. Externally, we advocate using an industry expert, such as Exponential-e, to audit third parties, evaluating and documenting the risk presented.
Consultancy deliverables include:

ORA (Own Risk Assessment) compliance with TPR
Exponential-e will build a statement of works, tailored to your pension scheme, to identify where cyber security can be improved, aligned to codes ADM15 & ADM16.

Internal risk mitigation, aligned to the Cyber Essentials accreditation.
Exponential-e will perform a readiness assessment that will prepare the scheme for the Cyber Essentials self-assessment that leads to certification.

External risk
mitigation via audit of third-party providers.
The Capita breach demonstrated that there is risk to pension schemes within the supplier base. Exponential-e will evaluate how your scheme’s data is being managed and offer advice to mitigate the risk and minimise your personal liability.

Documentation to support Effective System of Governance (ESOG).
Exponential-e will provide subsequent reports that will form part of your ESOG obligations to the Pensions Regulator.
vCISO & vDPO
If you don’t know where you are going, any road will get your there._Lewis Carrol
Schemes manage significant amounts of valuable data that traverses multiple organisations. The Pensions Regulator advises nominating a trustee to serve as a lead on data protection and the wider ramifications for policy, processes and IT security.
Our Virtual Chief Information Security Officer (vCISO) and Virtual Data Protection Officer (vDPO) services offer you direct access to the experience and expertise of a leading cyber security professional, who will take primary responsibility for your scheme’s compliance obligations and provide hands-on support around its data protection challenges, allowing you to stay ahead as new legal and regulatory developments impact your scheme’s operations.





The vCISO/vDPO will deliver all the following for your scheme:

Consult
Achieve and maintain compliance with all the IT and data protection regulations relevant to your scheme.

Advise
Advise the trustee responsible for data privacy impact assessments, including incident response planning and coordination.

Act
Act as single point of contact for you, the ICO and your stakeholders.

Maintain
Maintain comprehensive, accurate records of processing operations.




Endpoint Device Security
If the device is smart, it’s vulnerable_John Chambers (Former Cisco CEO)
The Pensions Regulator stipulates that the trustee responsible for a scheme’s IT is obligated to act to reduce the likelihood of cyber incidents and to detect when an incident occurs. A primary vulnerability of a scheme is the devices its trustees utilise.
Laptops, mobile phones, tablets, and any device that accesses scheme data are gateways for bad actors to execute malicious attacks. Exponential-e will provide the tools to minimise risk through appropriate and proportionate device and security solutions, delivering Peace of Mind as-a-Service to trustees, in compliance with the TPR’s section on Maintenance of IT Systems.
Exponential-e’s Endpoint Device Security portfolio will deliver:

Enterprise-grade device security solutions
Protect your existing laptops, mobile phones, and other devices from unauthorised access and malicious acts. Components of the solutions include multi-factor authentication, threat detection, anti-virus, monitoring and response software that is automatically updated in real-time, with no need for manual intervention.

Multi-factor authentication
Combine robust passwords and access authorisation via a second device to mitigate the risk of identity theft or social engineering being used to access sensitive data via laptops and mobile devices.

Laptop-as-a-service solutions
Provision of preconfigured laptops with the appropriate security software preinstalled, after which faults, thefts and losses are managed by Exponential-e, minimising both data loss concerns and administrative burdens, while helping comply with the TPR’s Maintenance of IT systems obligations: “Put a policy in place for maintaining, upgrading, and replacing hardware and software”.



Incident Response
The killer is being surrounded by a web of deduction, forensic science and the latest in technology._Inspector Clouseau, The Pink Panther
Cyber security is at the top of the Pensions Regulator’s agenda, and they recently issued guidance on how schemes should respond in the event of a cyber-related incident.
Exponential-e can offer support in the event your scheme is compromised by a cyber-attack, via a fast and effective incident response service. This is needed to establish the impact of the incident on your scheme’s functions and the resulting risk. Having an effective response that is documented and aligned to your scheme’s existing policies and controls can help mitigate personal liability and support effective reporting to the ICO and governing bodies, where required.
What services does Incident Response include?

Preparation
Planning to enable an agile, precise and comprehensive response to a breach.

Threat containment
Eradication of the threat including support for various types of breach, including ransomware and network intrusion.

Identification and preservation
Analysis of digital evidence at forensic level, with reporting of any suspected threats.

Legal standards of e-discovery
Investigation management services, with formal standards of reporting by experts to aid your scheme when dealing with regulatory enforcement action.

Subject matter expertise during litigation and reporting
Fulfilling data subject requests and responding to other requirements under GDPR and other data protection standards to governing bodies.
IT Security Training
If you know the enemy and know yourself, you need not fear the result of a hundred battles._Sun Tzu
IT Security Training is a highly effective option for organisations with a small number of people, but who own and operate high-value assets, such as pension funds.
We offer a universally accessible training course that enables your scheme’s trustees to clearly understand how the technology they use plays a key role in helping secure against the latest cyber threats. The training covers the methods attackers will leverage to exploit your scheme and the best practice to protect against cybercrime and bad actors.



We fully tailor each training programme to each scheme:

Bespoke IT training
Training directly aligned to trustees’ current level of cyber expertise, based on the initial GAP analysis conducted.

Learn best practice
Training on device security, email security, and how to avoid the common strategies employed by bad actors.

Phishing e-mail training
The practice of fooling recipients with malicious intent via email
Awareness training that emulates known tactics, techniques, and procedures, with simulations to test users.

Hacking fundamental training
Training aimed at the scheme’s designated IT lead - Create a better understanding of the holistic threats presented to their scheme and how they can offer effective guidance through both policy and leadership.
ABOUT US
Exponential-e:
Who we are and what we do
The Exponential-e Group has over 62 years of experience, credentials, and capabilities in delivering critical infrastructure to both the public and private sectors. The combined skills and expertise of the three companies now make ‘military-grade’ solutions more accessible and available to our partners, underpinning their own customer solutions.
Exponential-e Cyber Security Heritage
2002
Word-first innovation in connectivity
Core foundation delivering...
Your application is as good as your network
Your data is as good as your network
Your Cloud is as good as your network
2002
2006
The UK's most secure carrier network
2006
Multiple services / true Layer 2/3 services anywhere
2006
2006
Worlds first Virtual Private LAN (VPLS)
Offering the next generation of secure data and application transfer
2010
World-first bandwidth management tool from the Cloud
Manage your application across your network
2010
2010
Your Cloud is only as good as your network
The complementarity of next-generation networks and virtualisation projects
2013
Core network investments
Secure Cloud and data centres
2013
2013
Launch of our 'Clean side of the firewall'
Resolving enterprise data security and privacy issues
2014
Cloud and Network innovation resolves enterprise issues with Cloud adoption
2014
2017
Launch of our Cyber Security product portfolio
2018
24/7 UK-based Cyber Security Operations Centre (CSOC)
2018
2018
BS10012-PIIS standard for data management
2018
Exponential-e approved as HSCN, Stage 3 CNSP, since 2018
2018
2019
DDOS service across our infrastructure
2021
SOC 2 Type 2
2021
2021
Operate within List X facility (Top Secret)
2022
Biggest Cyber Security Vault solution in Europe
2022
2022
All staff background checked . 50+ staff developed, vetted and ten with top secret clearance


Accreditations and Frameworks
SOC2 - Type 2 Compliance
A SOC2 - Type2 Compliance is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. These reports are issued by independent third party auditors covering the principles of Security, Availability, Confidentiality, and Privacy.

PCI DSS
The PCI DSS is a set of comprehensive requirements for enhancing Network security. It is a multifaceted security standard that includes requirements for: Security management, policies and procedures, network architecture and their critical protective measures. This comprehensive standard is intended to help organisations proactively protect its Network.

Our Cyber Security Ecosystem
Cyber Security Advisory
Managed Services
Endpoint Protection
Identity & Access Management
Cloud Security
Cyber Security Advisory
CSOC - Cyber Security Operation Centre
SIEM - Security Incident & Event Management with Forensics & Remediation
Managed Vulnerability Scanning
Threat Monitoring & Intelligence
Simulated Phishing Attacks
with Training & Awareness
Penetration, Red Team
and Purple Team Testing
Applying our customer-first philosophy to the contact centre
Rolling 3 month average. Industry average: 17
Our commitment to delivering excellence
The world’s first real-time NPS - part of our longstanding customer service promise.
Through our own customer service platform, our customers are able to give us feedback quickly and easily, with a click of a button. Our Customer Support teams are immediately notified of feedback so they can respond instantly, in order to quickly closing the loop on any feedback that is less than excellent.
Our Technology Partners





































GET IN TOUCH
Are you ready to retake control of your cyber security and IT infrastructure?
Fill out the form to schedule your assessment and start building a more resilient, efficient, and secure digital foundation for your business.
Contact Sales: 0845 470 4001
Service & Support: 0800 130 3365
London Head Office
Manchester Office
*Calls to 0845 numbers will cost 7p p/m plus your phone company’s access charge.
All inbound and outbound calls may be recorded for training or quality purposes.