A 30‑year‑old man has been charged with launching a cyberattack on the German subsidiary of Russia's state-owned oil giant Rosneft. The cyberattack, which happened in March 2022 in the aftermath of Russia's invasion of Ukraine, crippled the company's operations and cost millions of euros in damages.
The UK's National Cyber Security Centre (NCSC) has warned the IT helpdesks of retailers to be on their guard against bogus support calls they might receive from hackers pretending to be staff locked out of their accounts.
A UK firm has been hit by a £3.07 million fine after being hit by a ransomware attack that exposed sensitive data related to almost 80,000 people, and disrupted NHS services.
The UK government has proposed extending its ban on ransomware payments to cover the entire public sector in an attempt to deter cybercriminal attacks and protect taxpayers.
Stoli Group USA, the US subsidiary of vodka maker Stoli, has filed for bankruptcy – and a ransomware attack is at least partly to blame.
The American branch of Stoli, which imports and distributes Stoli brands in the United States, as well as the Kentucky Owl bourbon brand it purchased in 2017, was hit by a ransomware attack in August 2024.
Although the rise in money criminals have generated through ransomware has risen by what may appear to be a small percentage amount (approximately 2% from US $449.1 million to US $459.8 million), this is in spite of disruption caused to ransomware-as-a-service operations such as LockBit and ALPHV/BlackCat by law enforcement agencies.
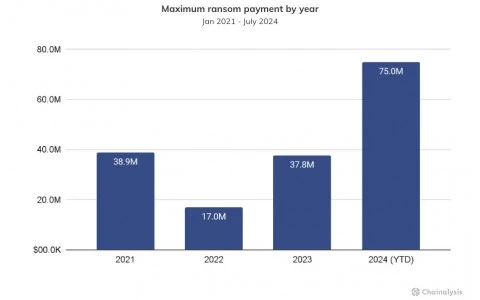
The figures for the first half of 2024 include the US $75 million reportedly paid to the Dark Angels ransomware gang by an undisclosed Fortune 50 company, in what was believed to be the largest ever single ransom payment made since records began.
The ballooning size of maximum ransom payments represents a 96% year-on-year growth from 2023, and a 335% increase from the maximum payment made in 2022.
Chainalysis's research reveals that the median ransom payment made in response to the most severe ransomware has rocketed from just under US $200,000 in early 2023 to US $1.5 million by mid-June 2024.
The researchers believe that this 7.9x increase in the typical size of ransom payment (a nearly 1200x rise since the start of 2021) suggests that larger businesses and critical infrastructure providers considered more likely to agree to make higher payments due to their greater access to funds and the more significant impact of downtime.
Against this backdrop, the study claims that ransomware victims are giving in to extortion demands less often. As it explains:
Posts to ransomware leak sites as a measure of ransomware incidents have increased YoY by 10%, something we would expect to see if more victims were being compromised. However, total ransomware payment events as measured on-chain have declined YoY by 27.29%. Reading these two trends in tandem suggests that while attacks might be up so far this year, payment rates are down YoY. This is a positive sign for the ecosystem signalling that perhaps victims are better prepared, negating the need to pay.
In short, ensuring that your organisation had prepared to respond to a ransomware attack is essential.
Many organisations underestimate the importance of having a robust incident response plan. But knowing how to respond, especially in those critical first 48 hours after a cyber attack, can be critical.
Do you worry your company won't know how to recover after a cyber attack? Has your business just been hit by ransomware and you're wondering what to do?
There's still hope.
Don't make the mistake of believing that your organisation will never be targeted. The right approach is to take proactive measures in advance - as it's not a case of whether your business will suffer the likes of a ransomware attack but when.
Make sure to read Exponential-e's step-by-step guide on ransomware remediation.
What's happened?
Recorded Future has reports that the British Government is proposing sweeping change in its approach to ransomware attacks.
Do you know Dmitry Yuryevich Khoroshev?
If you do, there's a chance that you might well on the way to receiving a reward of up to $10 million.
Law enforcement agencies across the US, UK, and Australia have named Dmitry Yuryevich Khoroshev as the mastermind behind the notorious LockBit ransomware group, estimated to have extorted $500 million from companies worldwide.
The international hotel chain Omni Hotels & Resorts has confirmed that a cyberattack last month saw it shut down its systems, with hackers stealing personal information about its customers.
In the aftermath of the attack, hotel guests reported that they had been forced to check in on paper, that room keys didn't work, and all phone systems and Wi-Fi were offline.
Any organisation that has tried to recover from a ransomware attack knows that it can be time-consuming and costly. Companies hit by an attack must choose between paying a ransom or recovering encrypted data from a backup.
Unfortunately, ransomware gangs are too aware that they can leverage significantly higher ransoms from their corporate victims if they have also compromise the company's backups. For this reason, we are seeing more and more cyber attacks targeting backups because they know that organisations desperately need them to recover if they want to avoid paying a ransom to cybercriminals.
In October 2023, the British Library suffered "one of the worst cyber incidents in British history," as described by Ciaran Martin, ex-CEO of the National Cyber Security Centre (NCSC).
The notorious Rhysida ransomware gang broke into one of the world's greatest research libraries, encrypting or destroying much of its data, and exfiltrating 600 GB of files, including personal information of British Library staff and users.